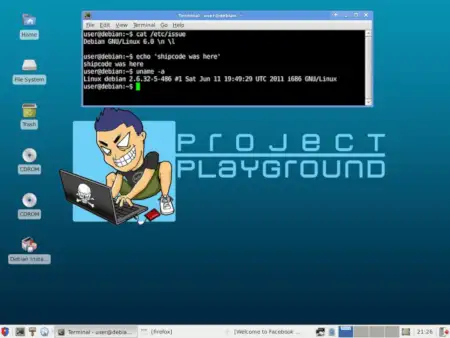
Web site: www.theprojectxblog.net (not active) Origin: Philippines Category: Security, Pentest Desktop environment: Xfce Architecture: x86 Based … Project PlaygroundRead more
security
Honeywall
Web site: projects.honeynet.org/honeywall/ Origin: USA Category: Security Desktop environment: CLI Architecture: x86 Based on: CentOS Wikipedia: … HoneywallRead more
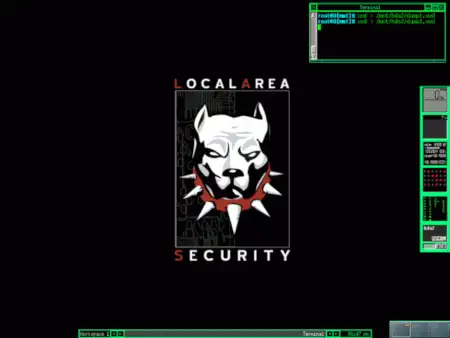
Local Area Security
Web site: www.localareasecurity.com (not active) Origin: USA Category: Security Desktop environment: Fluxbox Architecture: x86 Based on: … Local Area SecurityRead more
Live Hacking
Web site: www.livehacking.com/live-hacking-cd/ Origin: USA Category: Security, Pentest Desktop environment: GNOME Architecture: x86 Based on: Ubuntu … Live HackingRead more
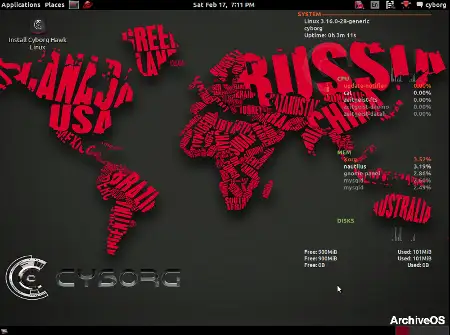
Cyborg Hawk
Web site: cyborg.ztrela.com Origin: India Category: Security, Pentest Desktop environment: GNOME Architecture: x86_64 Based on: Ubuntu … Cyborg HawkRead more